7 Easy Facts About Aws Backup Described
Wiki Article
Little Known Facts About S3 Cloud Backup.
Table of ContentsAll About Aws S3 BackupS3 Backup for BeginnersThe Ultimate Guide To Aws Cloud BackupGet This Report about Protection Against Ransomware
Information security is the procedure of protecting important information from corruption, compromise or loss and also providing the capacity to recover the information to a functional state need to something happen to render the information inaccessible or pointless. Information security guarantees that data is not corrupted, is available for accredited functions only, as well as is in conformity with relevant lawful or regulative demands (aws backup).The range of data protection, nevertheless, goes past the concept of data availability and functionality to cover areas such as data immutability, preservation, and deletion/destruction. Roughly speaking, information protection covers 3 broad categories, particularly, standard data protection (such as backup as well as recover copies), data protection, and also data privacy as shown in the Number below. Number: The 3 Classifications of Data Protection The principle of data protection is to deploy methodologies and also technologies to protect as well as make data offered under all circumstances.
g. cloning, matching, replication, pictures, altered block monitoring, and so on,) are offering an additional layer of information security along with typical backup. Modern technology developments mean that it is now common method to give continual data protection which backs up the data whenever an adjustment is made so that recovery can be near-instantaneous.
The information storage space sector looks at information security mostly from a technology point of view in what is required to maintain information safeguard and readily available. Information defense is specified by the European Union (EU) in a really various method and is commonly made use of where various other areas might make use of the term information privacy.
The Basic Principles Of Aws Cloud Backup
Data goes to the facility of service. https://docs.google.com/drawings/d/1FPgfdvuW8xBSarAtJwODOc5ah7N65pVDs5H7iu2jgOQ/edit. For several organizations, electronic adoption drives method. Information is necessary to fulfilling customer requirements, replying to sudden market shifts and also unexpected events. That's why information defense must get on your mind. Enterprises produce large amounts of data from several sources. The sheer volume as well as information of enterprise information developed during doing company calls for continuous interest to just how you shield and maintain it.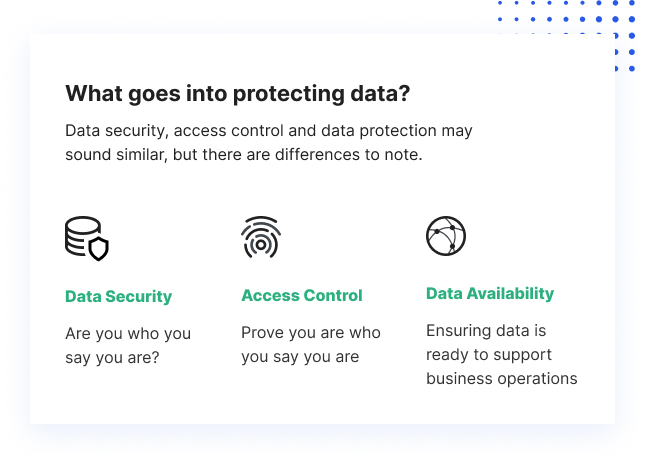
Today, it includes Io, T devices and also sensing units, industrial equipments, robotics, wearables as well as more. Data protection helps in reducing risk and enables a service or firm to respond quickly to threats. Data security is necessary since the overall number of computing devices raises yearly, and also computing is now more intricate.
2 ZB of information was created or duplicated. Not all data produced in 2020 was stored, however IDC recommends there is adequate proof storing a lot more data could profit business.
The Single Strategy To Use For Data Protection
The manufacturing industry tends to invest less resources in protecting industrial procedures technology (OT) than in their venture networks. That leaves OT systems open up to jeopardize. These OT systems consist of self-driving lorries, robotics, Industrial Io, T tools as well as sensing units. Essential infrastructure depends on commercial control systems as well as a great deal of different OT systems to work.The production sector is a popular assault target, as well. In 2020, production, power as well as healthcare sectors encountered the highest possible price of assault according to IBMs Annual X-Force Danger Index. Protecting business networks without giving the very same interest to OT and devices opens them for a strike. Digital assets are financially rewarding targets, also much more so as even more services overcome electronic development initiatives connecting more solutions.
Information safety for supply chains as well as third-party accessibility to systems is important to secure them from cyberattacks. Stabilizing compliance with meeting organization objectives can be a difficulty if you do not have an information defense technique in area.
The order concentrates on actions to strengthen cybersecurity via bringing essential infrastructure as well as federal government networks as much as contemporary standards. This will only obtain even more facility as the federal government establishes brand-new regulations and even more carefully applies older guidelines. A take a look at consumer data privacy laws by state discloses unequal electronic personal privacy expectations (protection against ransomware).
The Best Strategy To Use For Aws Backup
There stay no sweeping federal legislations on consumer information personal privacy securities. Data protection description and information protection are comparable but distinctive.A detailed information safety and security strategy secures electronic assets versus assault while accounting for and also securing versus expert risks. Releasing data security devices and modern technologies provide businesses a means to evaluate critical information at its storage locations. Risk actors took the opportunity to seek out openings, resulting in the costliest year for information breaches.
Report this wiki page